The critical need to keep your account passwords distinct and the value of your personal information 07/23/2019
Jul. 23, 2019 by vspiars
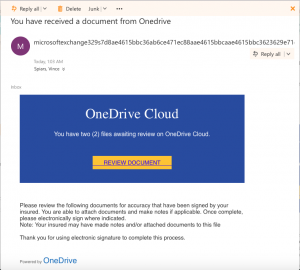
These 2 seemingly distinct topics are very related. In the last 10 days I have been alerted to 16 data breaches that date back to 2017 and contain some number of accounts that have @wesleyan.edu in their account information. The reasons for the delayed notifications can be varied–companies are just finding out, companies don’t want to tell customers, companies are still sorting-out what data has been compromised, … This goes back to three previous articles that speak to the need for distinct passwords for each online account you have, the accompanying need for a Password Manager and finally, for Muti-factor/Dual-factor/2-factor Authentication. Her is the list of what I have been notified of in the last 10 days, alone.
Flash Revolution (2019 breach)
Stronghold Kingdoms data breach
GameSalad data breach
Armor Games data breach
Roll20 data breach
Artvalue data breach
EatStreet data breach
Bulgarian National Revenue Agency data breach
YouNow data breach
Animoto data breach
SHEIN data breach
piZap data breach
Netlog data breach
Evite data breach
“Hulu and HBO accounts”–A Paste of accounts was found with this title on the web sites frequented by criminals. This is not to say either Hulu nor HBO have been compromised
MindJolt data breach
The data breaches provide varying degrees of value to thieves based on what they contain. But with enough data points a pretty complete picture of a person can be created. The source of the 2017 report of ID value that I came across below came from the same Equifax that was breached and lost all of the Credit Bureau data for 147 million accounts. Anyone else see the irony?
Personal data and identity theft have been a concern for years. However, due to these numerous breaches I came across some very interesting statistics.
- Social Security number: $1
- Credit or debit card (credit cards are more popular): $5-$110
- With CVV number: $5
- With bank info: $15
- Fullz info: $30—-Note: Fullz info is a bundle of information that includes a “full” package for fraudsters: name, SSN, birth date, account numbers and other data that make them desirable since they can often do a lot of immediate damage.
- Online payment services login info (e.g. Paypal): $20-$200
- Loyalty accounts: $20
- Subscription services: $1-$10
- Diplomas: $100-$400
- Driver’s license: $20
- Passports (US): $1000-$2000
- Medical records: $1-$1000*
*Depends on how complete they are as well as if its a single record or an entire database
- General non-Financial Institution logins: $1
Because these data breaches are so frequent the value of the once coveted SSN (Social Security Number) is now, $1. The most recent statistic I heard was a 2018 report (podcast) of $.05. A nickel but I can not find that written siting. The point in either case is there is so much data available on us that the value of things has plummeted in many cases. But your bank account, full medical records and passport information still fetch a fair sum. Making it as hard as possible for the bad guys to get your information is the best we can do if you have to provide that data. But if you do not need to put in information then do not. Do not volunteer anything not specifically, requested. And if it is a request for your SSN, Drivers Lic number, bank acct number(s) or passport number then ask why it is needed. If it seems suspect then stop, cancel the process and get the answer. If it is a form in an office then ask the desk attendant. As companies hemorrhage data the best we can do to protect ourselves is to secure the information from simple access and limit what is provided.